Configuring Keycloak To Require A OTP
Two factor authentication is becoming increasingly popular, requiring a user to authenticate with their credentials and then provide a One Time Password as the second factor. Often times this OTP is sent using a SMS text to a mobile phone number - if you talk to the experts, sure it's an extra level of security but SMS texts are not entirely secure...
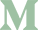
So, what can we do instead? Well, we can use a Mobile Authenticator app and that's what we're going to configure Keycloak to do. Open the Keycloak administrator console, ensure you're on the correct realm and select Authentication from the menu on the left. On the Flows tab, use the drop down in the top left and select Browser.
Then, in the second column, towards the bottom, you'll see "Browser - Conditional OTP" and we want to change that from Conditional to Required as below:
There's no need to save or anything, we're done on configuring Keycloak.
If you want to explore the OTP options in Keycloak a bit more, select the OTP Policy tab and check out the help icons and documentation. The settings there were left as default for the rest of this article.
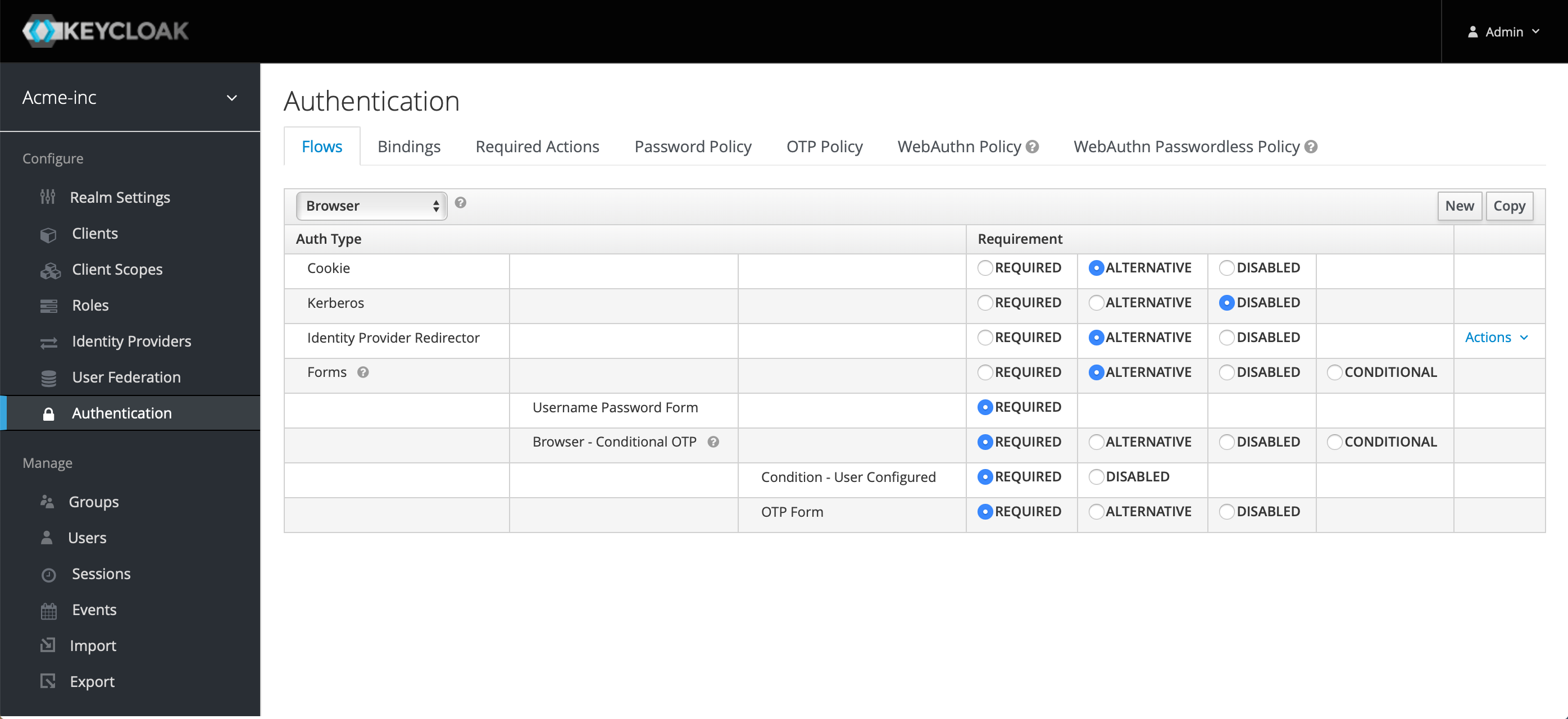
Mobile Authenticator Setup
Keycloak says it supports two authenticator apps, FreeOTP and Google Authenticator. Go ahead and download one of those to your mobile device from your applicable App store if you wish. We already use the Microsoft Authenticator app and so we were curious what would happen if we used that. Whatever app you choose, the process below is the same. Open your app on your mobile device so it's ready.
Now try opening your FileMaker database on your computer, click on the Keycloak button in the sign in dialog and as before a browser window will open asking you to log in. Type in your credentials and click Sign In, and this time, instead of being redirected back to your FileMaker Server you'll be presented with the screen below, asking you to set up your authenticator app.
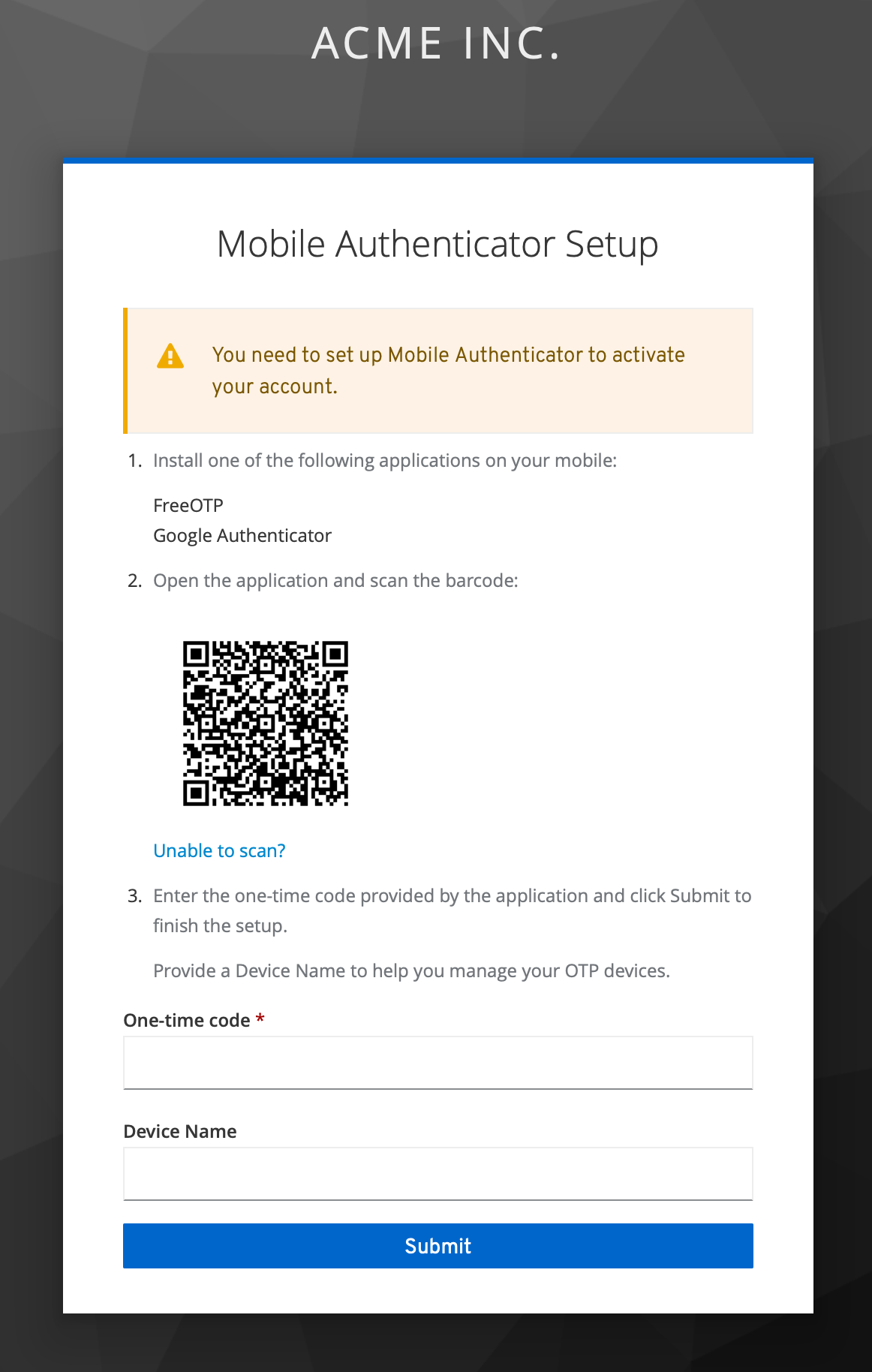
Back in your Mobile Authenticator app, choose to add an account. The screenshots below are from the Microsoft Authenticator app, but yours should be similar:
We're going to choose the Other option and when we do so, we're prompted to scan a QR code:

And fancy that, on our Keycloak Mobile Authenticator Setup webpage, we have a QR Code displayed. If you scan that QR code, it should add the account to your app and provide you with numbers that change every 30 seconds or so:
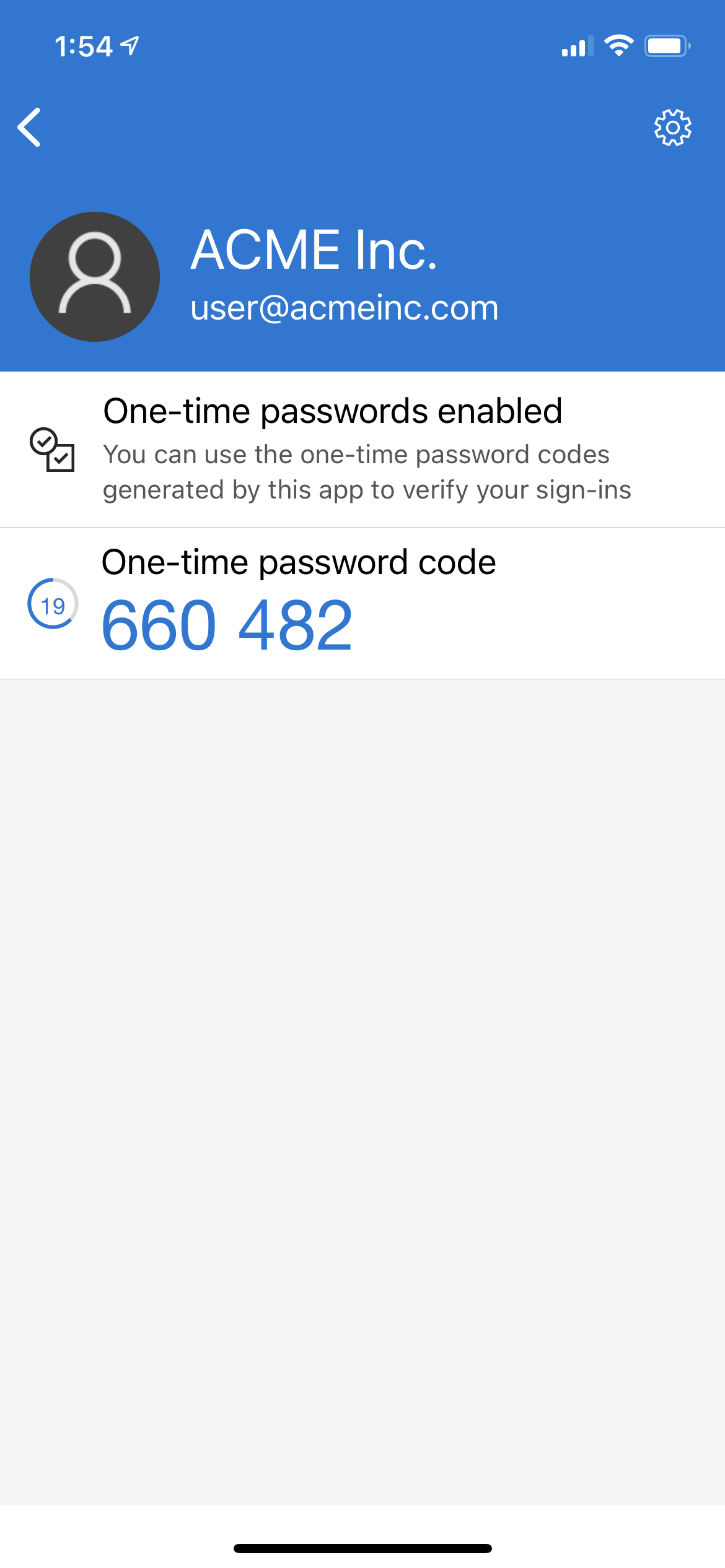
Take that code and enter it on the Keycloak page and add a name for the device your authenticator app is installed on. Assuming the code is still valid, you will once again be authenticated into the database.
If you want to test this again, you'll probably need to go to the Users area in Keycloak, click View All Users, select the user you are testing with, choose the Sessions tab and click "Log out all sessions". This will then prompt you to log in again when you try opening the database.
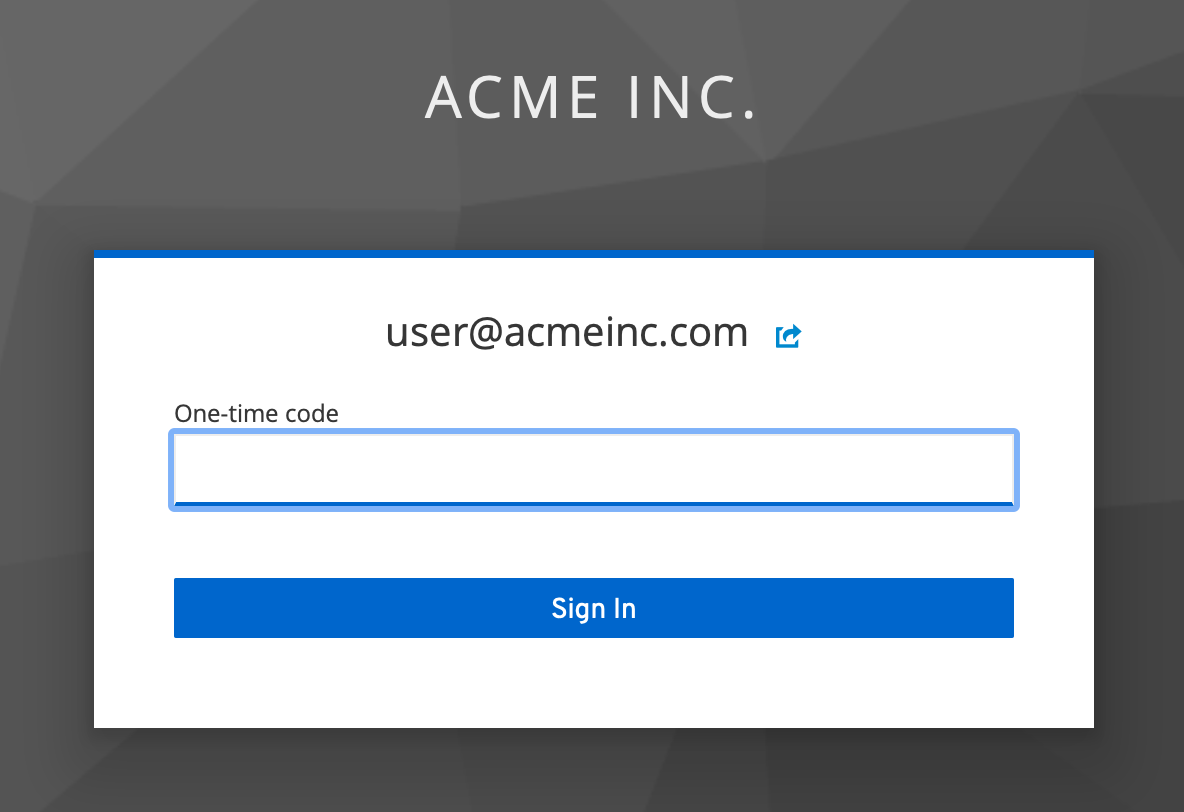
When we do that, after entering our credentials, we're presented with a much simpler dialog requesting the One Time Password from our authenticator app.
Summary
Setting up a second level of authentication in Keycloak has been pretty simple and helps ensure that the user that is trying to gain access to the database is who they say they are. This is not something we can do natively within FileMaker, so we're already leaps and bounds ahead, security wise, by using Keycloak. There are other authentication options and we hope to explore those in a future article. Next up, what if the Keycloak log in browser window doesn't align with your corporate identity? In our next article, part 8 of our Keycloak series, we'll find out how to adjust this.